Adding Identity Providers
5 minutes to readCaspio Directories supports SAML 2.0 single sign-on (SSO) as the method of authenticating users from trusted identity providers. SAML stands for Security Assertion Markup Language. It is an open standard based on XML used to authenticate users and authorize their access to web-based applications. This standard is commonly adopted to allow users to access multiple applications with a single set of login credentials. For instance, it can be used in enterprise environments, where employees require access to multiple applications across different domains, resulting not only in a simpler user experience but also better security due to improved management of user access and authentication policies.
SAML is based on the concept of transferring identity data between two parties: an identity provider (IdP) and a service provider (SP).
- Identity provider (IdP) carries out the authentication process and passes the user’s identity and authorization level to the service provider (SP).
- Service provider (SP) relies on the identity provider’s trust and authorizes a given user to access the specified resource.
In this section, we treat a Caspio directory as a service provider, which requests external trusted identity provider to authenticate users. In the authentication flow below, we use the user portal as an example of a resource a user is attempting to access. However, any application protected with a directory could be used.
Note: If you want a Caspio Directory to act as an identity provider, you need to configure App connections. Learn more.
Authentication flow
- The user logs into the user portal from a browser. If that user is assigned to IdP, the SAML flow is initiated.
- The directory responds by generating a SAML request. SAML request includes, among others:
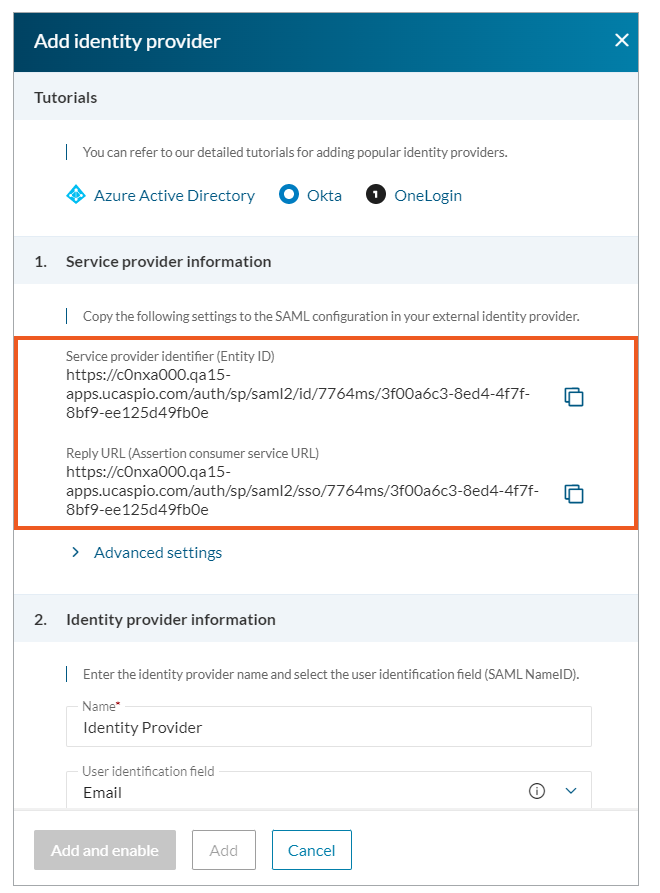
- Service provider identifier (Entity ID) – it enables the IdP to identify the user portal among other service providers.
- Reply URL or Assertion Consumer Service URL – a location to which the IdP sends the response after a user signs in.
- The browser redirects a user to a Single sign-on URL of the IdP.
- IdP parses the SAML request and authenticates the user.
- When the user is authenticated, IdP generates a SAML response.The response includes, among others:
- Identity provider identifier – it enables the user portal to identify the IdP.
- User identifier (NameID) – it is typically an email address.
- IdP returns the encoded SAML response to the browser.
- The browser sends the SAML response to the user portal for verification.
- If the verification is successful, the user will be logged into the user portal.
As shown above, communication between the IdP and SP in the SAML flow requires redirections to the places (URLs) known by both parties. They are:
- For service provider: Service provider identifier (Entity ID) and Reply URL.
- For identity provider: Identity provider identifier and Single sign-on URL.
The procedure below describes how to add a SAML identity provider to Caspio Directories. In order to configure an identity provider, you will need to place the links mentioned above in the appropriate places:
- The Service provider identifier (Entity ID) and Reply URL/Assertion Consumer Service URL links should be placed in an external IdP.
- The Identity provider identifier and User identifier (NameID) links should be placed in Caspio.
Steps to add an identity provider
If your identity provider is Microsoft Entra ID, Okta, or OneLogin, click the relevant link to configure the identity provider using our dedicated tutorial.
For other identity providers, follow their instructions on enabling single sign-on using SAML.
Before you begin:
Sign-in to an external admin provider with admin rights and set up an account.
STEPS IN EXTERNAL IDENTITY PROVIDER
- In an external identity provider, create a new application which will be used to connect with the Caspio directory.
- Select SAML as the single sign-on method and configure the general settings of your app, such as name or logo.
STEPS IN CASPIO
- In Caspio directories, in the Identity providers tab, click Add identity provider.
You will need the links from Caspio 1. Service Provider Information section in the next step to configure the external identity provider.
STEPS IN EXTERNAL IDENTITY PROVIDER
- Place the links for Service provider identifier (Entity ID) and Reply URL from the previous step in the appropriate places in your external app.
In the next steps, you will need the links from your external IdP, that is an Identity provider identifier and Single sign-on URL.
STEPS IN CASPIO
- In the 2. Identity Provider Information section:
-
- Enter the name and select a user identifier. We recommend using the default Email field.
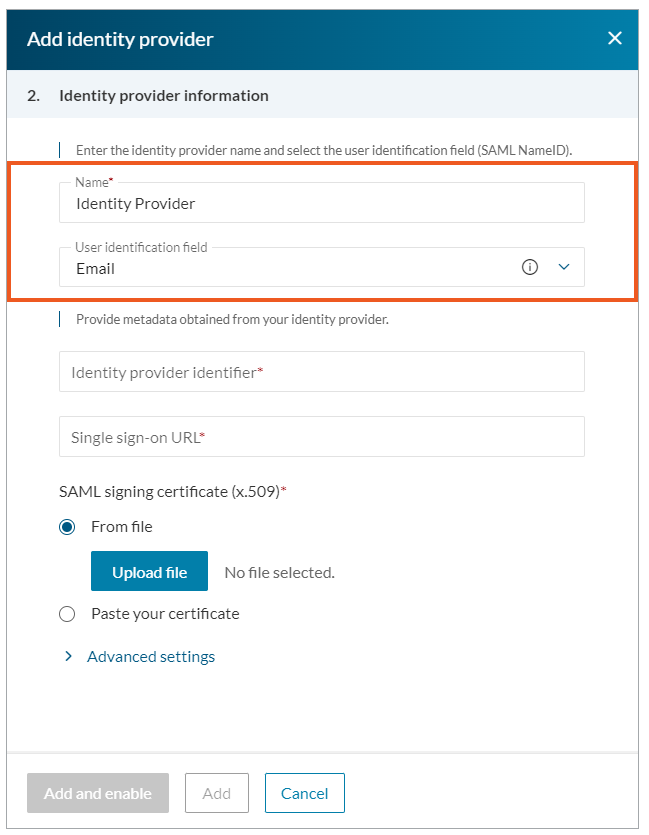
- Place the Identity provider identifier and Single sign-on URL links in the Identity provider identifier and Single sign-on URL fields.
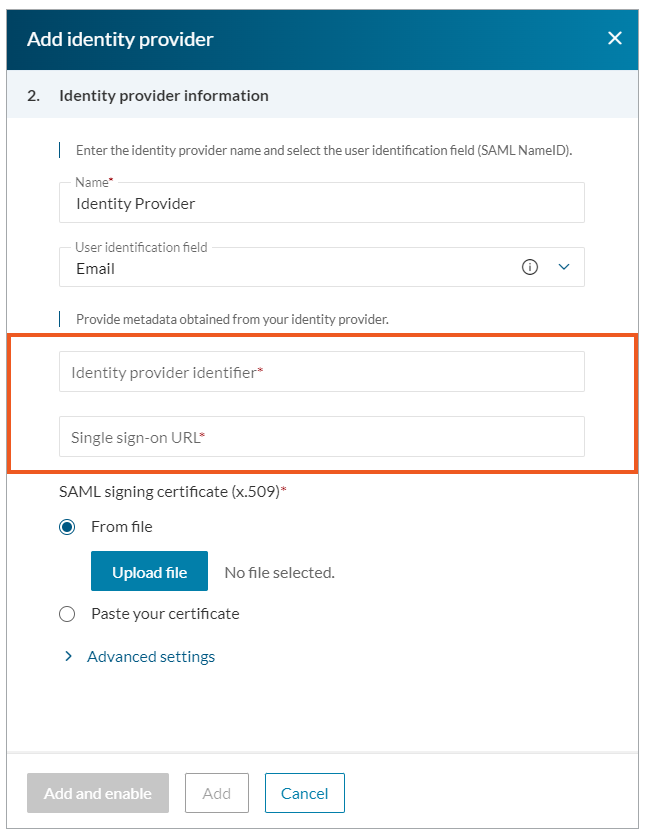
- Enter the name and select a user identifier. We recommend using the default Email field.
STEPS IN EXTERNAL IDENTITY PROVIDER
- Download x.509 Certificate from your external app.
STEPS IN CASPIO
- Paste a downloaded certificate into Caspio, in the SAML signing certificate (x.509) section.
- Click Add and enable.

