Tutorial: Adding Microsoft Entra ID (formerly Azure AD) Identity Provider
5 minutes to readThe following article will guide you on how to add an Azure AD identity provider. By doing that users in your organization will be able to access Caspio apps using credentials managed by Azure AD and sign out of both a Caspio directory and Azure AD with a single action.
Before you begin:
Sign in to Azure Active Directory with admin rights and set up an Azure AD account. Your users can be authenticated to Caspio apps by creating a new enterprise application in Azure AD.
STEPS IN CASPIO DIRECTORIES
- In Caspio directories, in the Identity providers tab, click Add identity provider.
Links from the 1. Service provider information section will be needed later to configure the external identity provider.
STEPS IN AZURE AD
- In Microsoft Azure, click on the menu in the top left corner and select Azure Active Directory.
- Under Manage Azure Active Directory, click View.
- In the left menu, select Enterprise applications.
- In the upper menu, click New application.
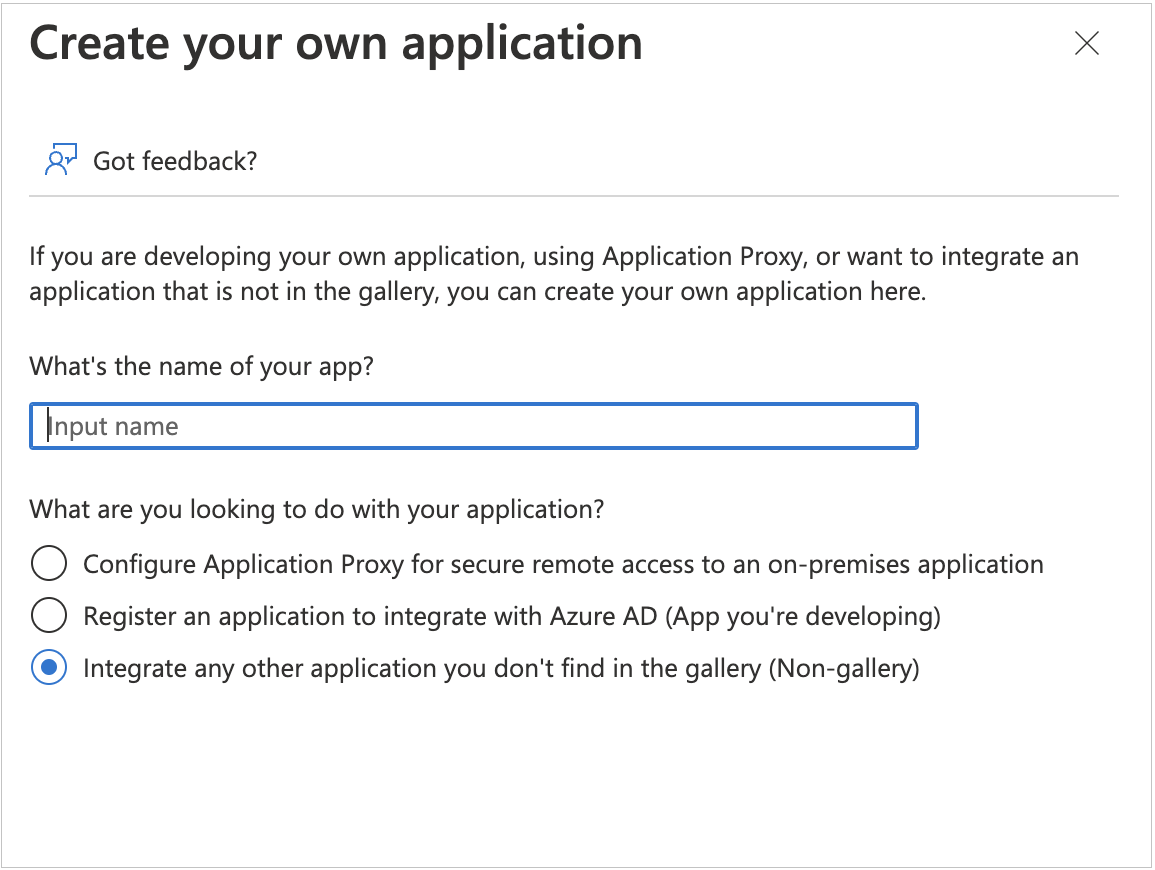
- In the Browse Azure AD Gallery screen, select Create your own application.
- Name your app.
- Select Integrate any other application you don’t find in the gallery (Non-gallery).
- Click Create.
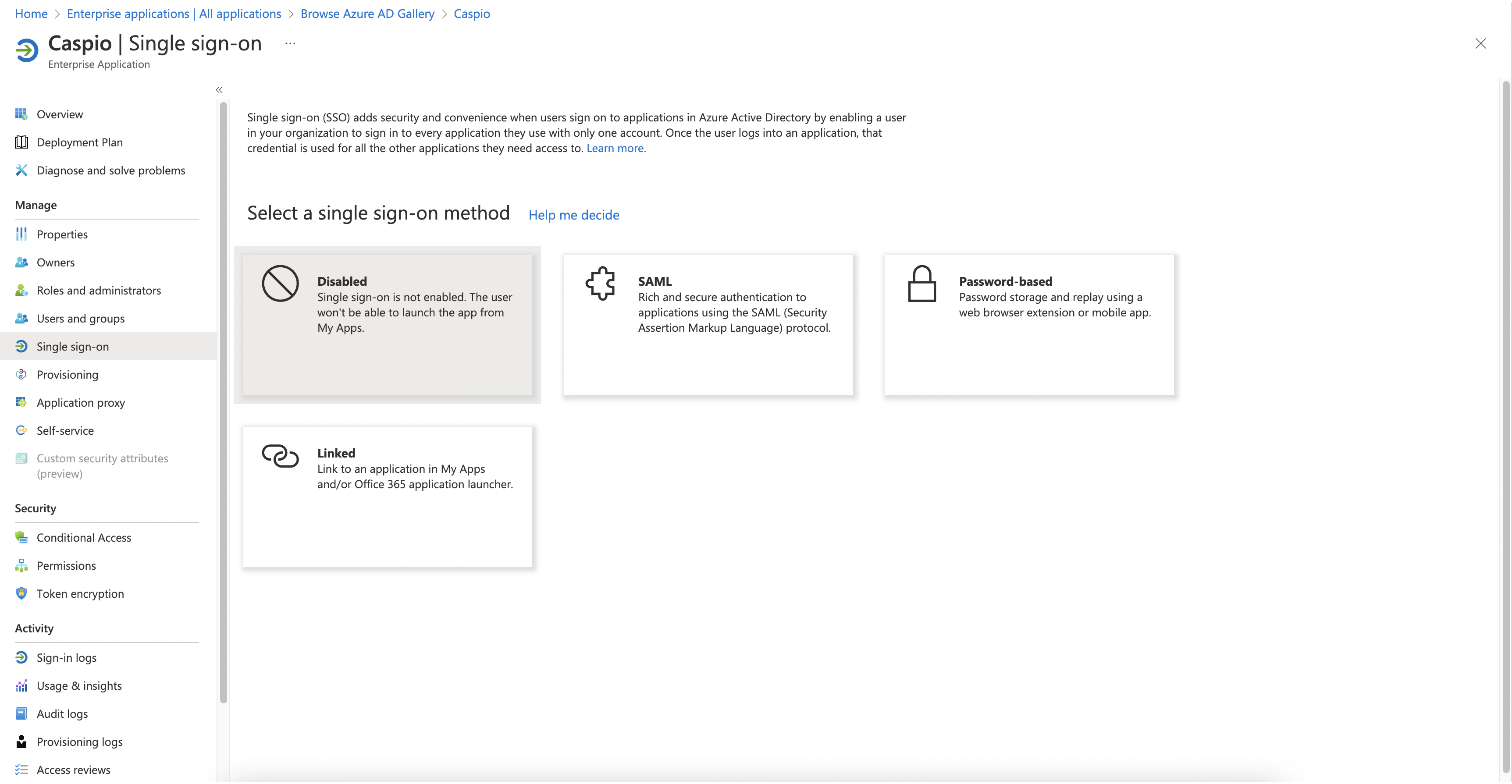
- In the overview page of a newly created enterprise app, select the Set up single sign on tile.
- Select SAML as the single sign on method.
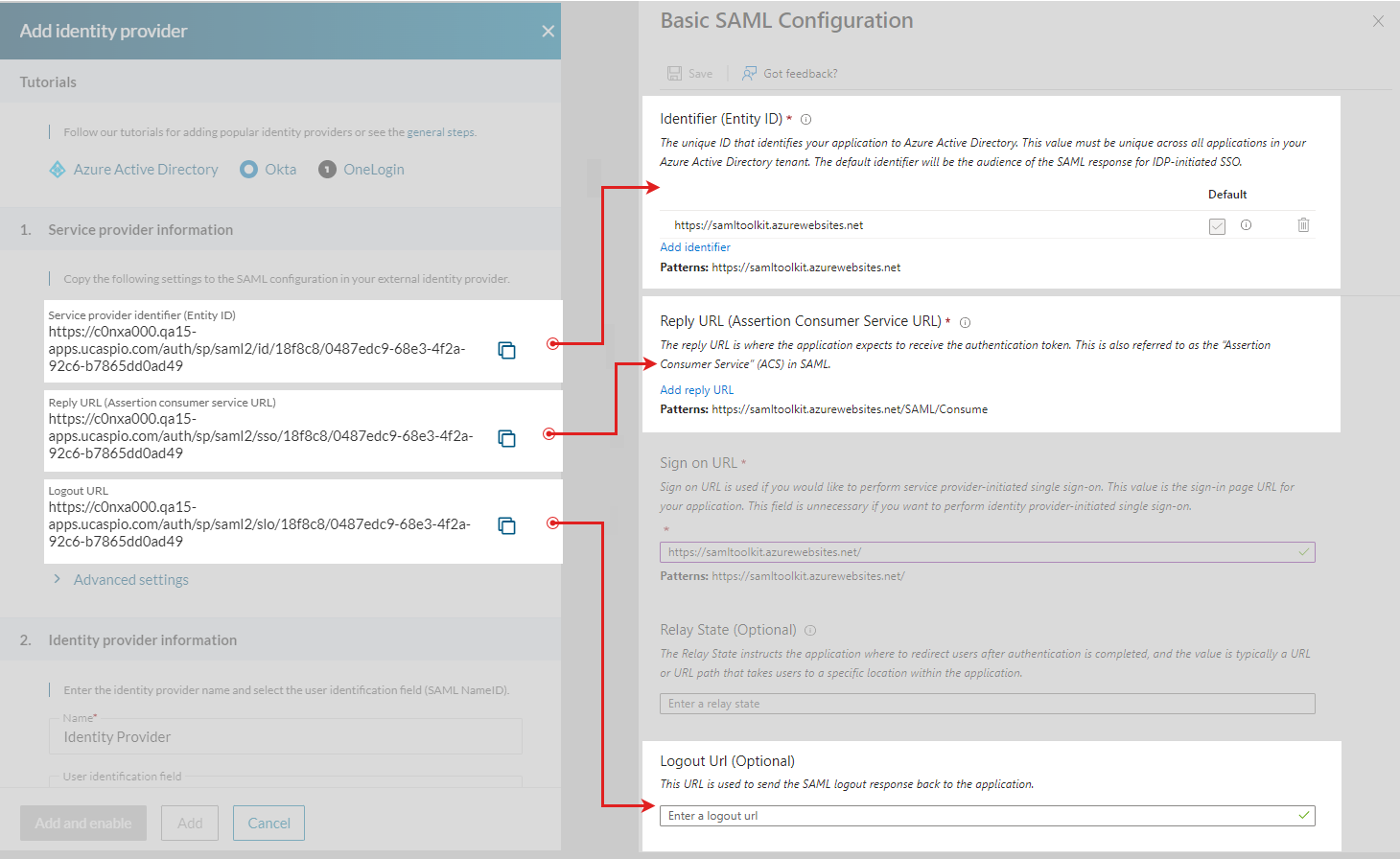
- In Azure AD, edit 1. Basic SAML Configuration and enter links from Caspio service provider information section according to the following table:
| Caspio → Service provider information | Azure AD → Basic SAML Configuration |
|---|---|
| Copy the Service provider identifier (Entity ID) URL... | …and paste it into Identifier (Entity ID) field in Azure. |
| Copy the Reply URL (Assertion consumer service URL)… | …and paste it into the Reply URL (Assertion consumer service URL) field in Azure. |
| Copy the Logout URL… | …and paste it into the Logout URL (Optional) field in Azure. This setting automatically signs users out of Caspio when they sign out of Azure. |
Note: Setting the logout URL to enable single logout is optional but recommended because it increases application security.
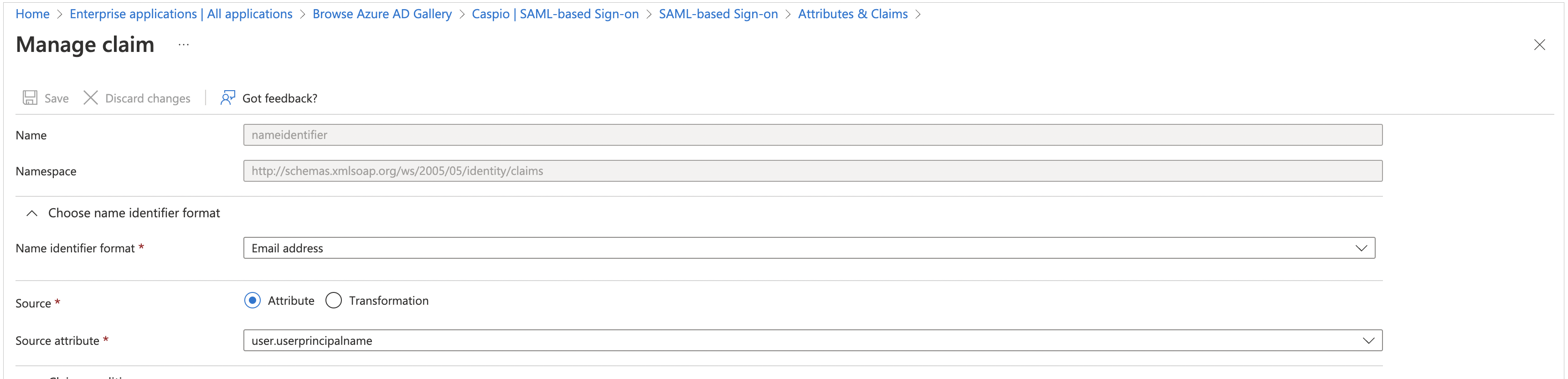
- In the 2. Attributes and Claims section, perform the following actions:
- Edit Attributes & Claims and click Unique User Identifier (Name ID).
- Select user.mail as Source attribute and click Save.
- In the 3. SAML Certificates section, download the Certificate (Base64). You will need this text in step 13c
- In Azure, open the Set up your application section. You will need it in step 13b.
STEPS IN CASPIO DIRECTORIES
- In Caspio directories, go to the identity provider you are adding and perform the following steps:
- Enter the name and select a user identifier in 2. Identity provider information. We recommend using the default Email field. If you use a different user identifier, please configure it also in the 2. Attributes and Claims section of Azure AD.
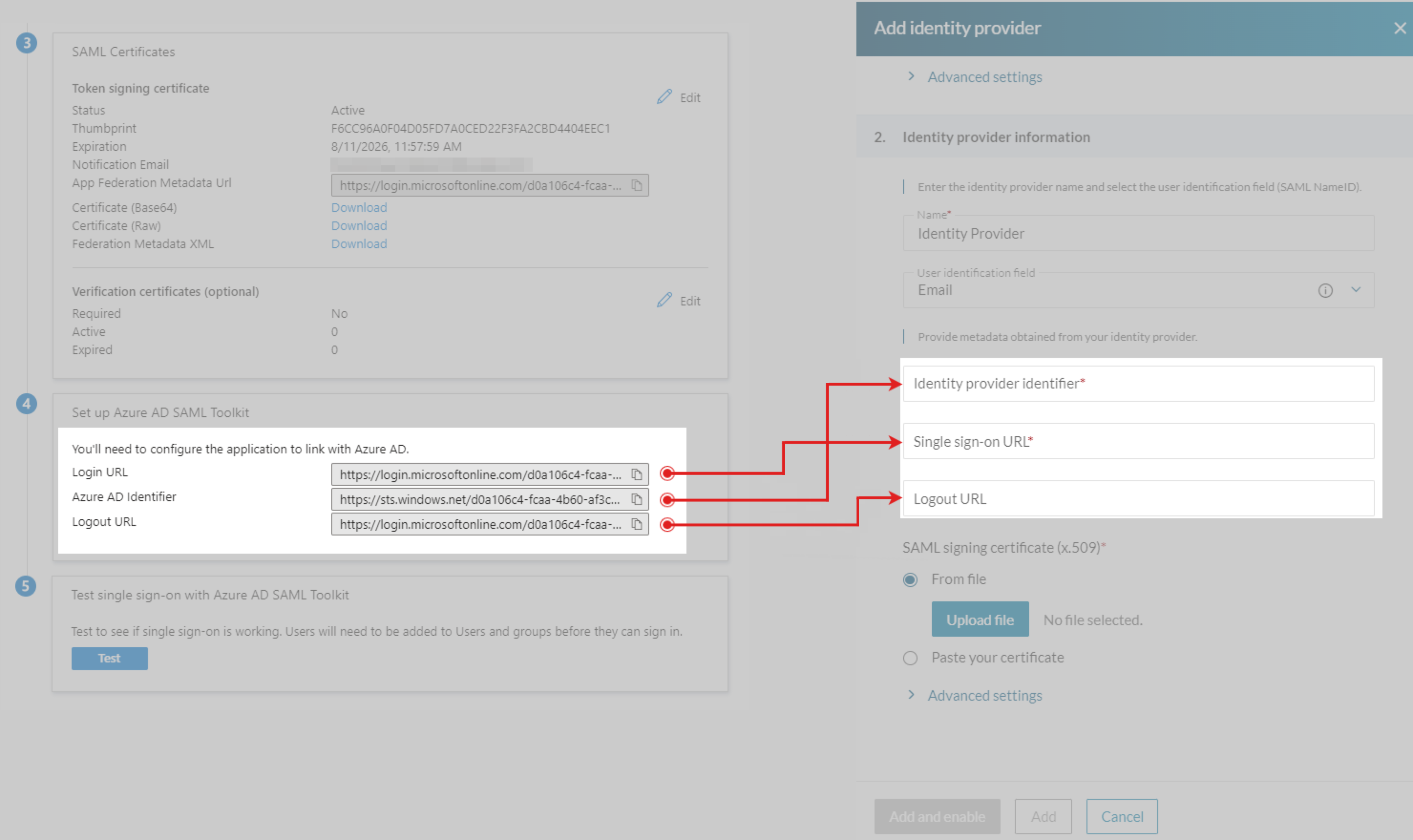
- Provide the copied links from step 12 according to the following table:
| Azure AD → Set up your app | Caspio → Identity provider information |
|---|---|
| Copy the Login URL link… | …and paste it into Single sign-on URL field in Caspio. |
| Copy the Azure AD Identifier link… | …and paste it into the Identity provider identifier field in Caspio. |
| Copy the Logout URL link… | …and paste it into the Logout URL field in Caspio. This setting automatically signs users out of Azure when they sign out of Caspio. |
Note: Setting the logout URL to enable single logout is optional but recommended because it increases application security.
- In the SAML signing certificate (x.509), upload a certificate from step 11.
- Click Add and enable.
Setting Single Sign-out
You can configure single logout to sign out end users of both a Caspio directory and Azure AD with a single action.
To automatically log app users out from a directory when logging out from Azure AD, copy the Logout URL link from the 1. Service Provider Information section in Caspio and paste it in Azure AD > 1. Basic SAML Configuration > Logout URL (Optional).
To automatically log app users out from Azure AD when logging out from a directory, copy the Logout URL link from the 4. Set up section in Azure AD and paste it in Caspio > Identity provider information > Logout URL.
Learn more about configuring SLO.
Testing Azure AD Identity Provider Configuration:
- Assign a user to an app in Azure ID:
- In the left menu, select Users and groups.
- In the upper menu, select Add user/group and open the list of all users and groups by clicking None selected.
- Select a user from the list and click Select → Assign.
- In the Add assignment screen, assign a user to an app.
- Add a user in Caspio directories:
- In the Users tab, create a user.
- Fill in an email address of the testing user from Azure AD (step 1c of the testing procedure). User email in Azure AD and Caspio directory must match to authenticate a user.
- Select sign-in method as per the identity provider name set up in step 6 above.
- Sign in to the user portal with Azure AD:
- In Caspio directories, select User portal.
- In the User portal URLs, click the Settings URL.
- In the login page of a user portal, enter the email address of the newly created test user in Caspio directory.
- In Azure AD login page, sign in with the Azure credentials.
- You should be redirected to the Settings page of the user portal where you can see the profile information of the logged in user, including the email address.

